The Hidden Dangers of Mixing or Overcentralizing Secrets in Azure Key Vault


In the world of cloud security, Azure Key Vault stands as a fortified fortress, guarding our most sensitive data and secrets.
With its robust encryption and access control capabilities, Azure Key Vault offers a secure and convenient way to store and manage secrets.
However, in our quest for convenience, we often stumble into a common pitfall: mixing all sorts of secrets in one vault without understanding the consequences.
In this blog post, we'll explore the importance of not mixing various types of secrets in Azure Key Vault and demonstrate why over centralization can be equally dangerous.
The Allure of Azure Key Vault
Azure Key Vault is a versatile solution for securing secrets, which include sensitive information like passwords, connection strings, and API keys. The appeal lies in its ability to centralize these critical assets, making it easier to manage and secure them.
The Pitfall: Mixing Different Types of Secrets
One common mistake that organizations make is mixing various types of secrets in one Azure Key Vault. While it's possible to store all your secrets in a single vault, this practice can have unintended consequences.
The Risks of Mixing Different Secrets
The issue arises when you have broad permissions, such as 'get' for a vault that contains various types of secrets. An entity with 'get' permission can retrieve any secret in that vault.
This can be a substantial security risk, as it could lead to unauthorized access to sensitive secrets by users or applications that should not have access to them. A broad permission that allows access to one secret inadvertently provides access to all secrets in the vault.
Best Practices for Azure Key Vault Secrets
A common recommendation is to use a vault per application per environment.
Also consider these best practices:
- Segregate Secrets: Create separate vaults for different types of secrets. This segregation limits the impact of broad 'get' permissions, reducing the risk of unintended access.
- Implement Least Privilege: Grant the minimum necessary permissions to entities. Review and audit permissions regularly to ensure they align with your security policies.
- Educate Your Team: Ensure that your team understands the potential risks of broad permissions and the importance of segregating sensitive assets.
- Monitor and Audit: Implement comprehensive monitoring and auditing to detect unusual or unauthorized access to your vaults.
A Word of Caution: The Pitfalls of Overcentralization
While we've discussed the potential dangers of mixing various types of secrets in a single Azure Key Vault, it's equally important to be wary of overcentralization. Storing secrets of the same type in one vault can create its own set of security challenges.
Imagine a scenario where you've adopted Infrastructure as Code (IaC) to maintain a systematic and reproducible deployment process for all your Azure SQL servers. You've made the choice to centralize server admin passwords in a specific vault, possibly guided by a well-documented naming convention shared across your organization.
Here's the catch: by centralizing all these highly specific secrets in one place, you inadvertently create a potential security vulnerability. Your meticulously documented naming conventions and shared resources, such as Confluence pages, might inadvertently provide a roadmap for those with access to the vault or any Azure resource linked to it.
Wait, why any Azure resource linked to it ?
The Power of System-Managed Identities: A Double-Edged Sword
Indeed, there's an additional layer of complexity that deserves our attention: system-managed identities. These managed identities are powerful tools that simplify access to resources and services in Azure. However, they can also be a double-edged sword when it comes to security.
System-managed identities, such as those associated with Azure services like Data Factory, can make accessing Key Vault incredibly convenient.
Let's take an example: you've granted 'get' permissions to a Data Factory instance for retrieving secrets from a vault. This is what I have done for the factory named 'mpi-ngi-d' in the following exhibit.
Note that my own account does not have 'get' or 'list' permission on that Vault.
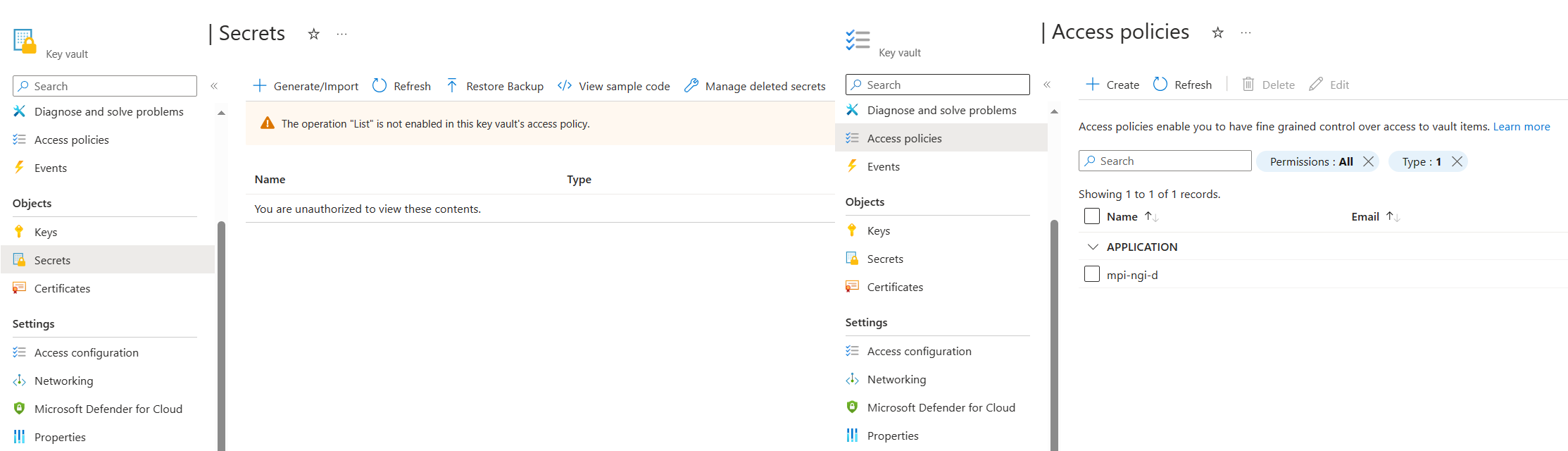
Now, any developer with access to that Data Factory can write a straightforward pipeline that fetches a secret using the factory's identity. While this simplifies the development process, it's essential to understand that the convenience comes with potential risks.
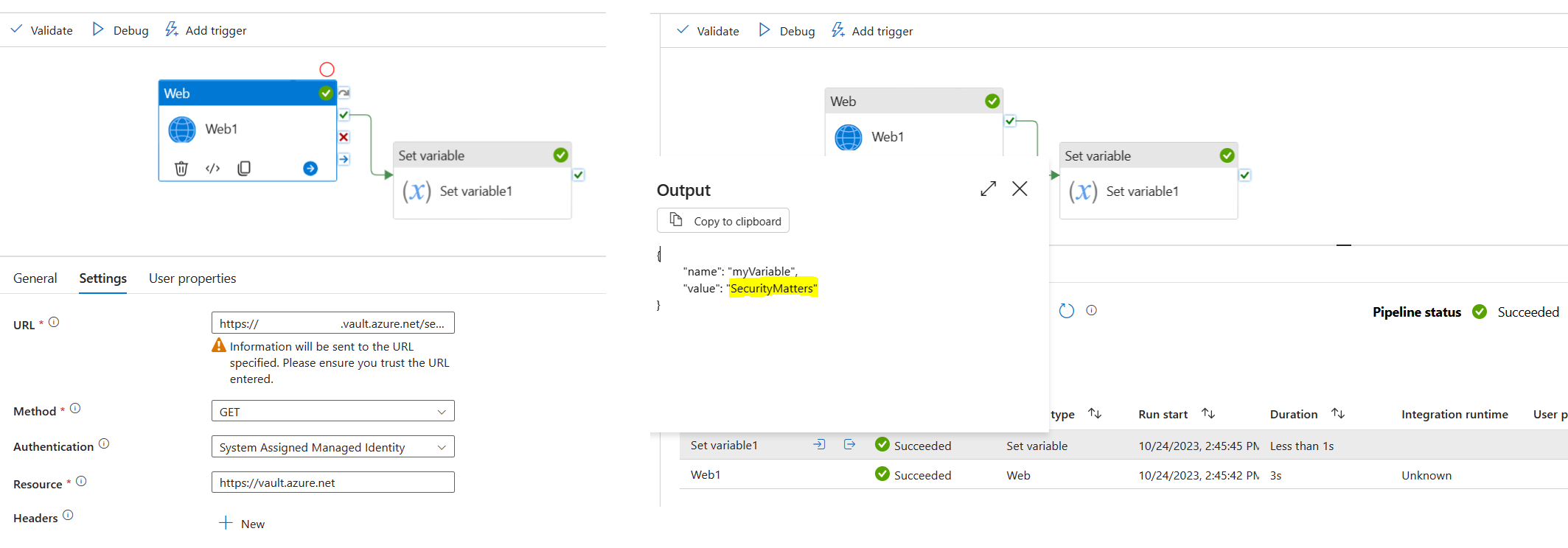
Developers, whether intentionally or inadvertently, might access sensitive data without the need for additional credentials or permissions. In this particular example, by setting the authentication to "System Assigned Managed Identity", I could fetch a secret, despite the fact that I don't have access to that vault myself.
Conclusion: Safeguarding Your Secrets
Azure Key Vault is a valuable resource for securing sensitive data, but its effectiveness relies on how it's used. Mixing various types of secrets, keys, and certificates in a single vault without a deep understanding of permissions and access risks can expose your organization to security vulnerabilities.
By following best practices and being vigilant in your approach, you can maintain the delicate balance between security and convenience in the realm of Azure Key Vault.
